Data Anonymization vs Data Masking: Compliance, ROI, and Risk Explained

Privacy mistakes rarely break systems; they break reputations. Firms lose prospects, partners, and market value the moment personal data leaks. A single breach now costs USD 4.88 million on average Source: IBM Cost of a Data Breach Report 2024.
Many companies already rely on platforms for intelligent document processing, yet they still swap “anonymization” and “masking” as if the two are interchangeable.
- Are you sure your reversible masking process satisfies GDPR’s “irreversible” test?
- Can your analytics squad trust masked data without breaking consent rules?
- How much could a wrong choice add to your breach bill or invite a €1.2 billion penalty?
This guide compares both techniques, shows real costs, and offers a clear decision framework so you can move data projects forward with confidence.
Key Takeaways
- Anonymization is permanent; masking can be reversed.
- Use anonymization for public data sharing and research.
- Pick masking for testing, QA, or role-based internal views.
- A five-question checklist helps teams choose the right path.
- KlearStack automates both methods through template-free AI.
What is Data Anonymization and Data Masking?
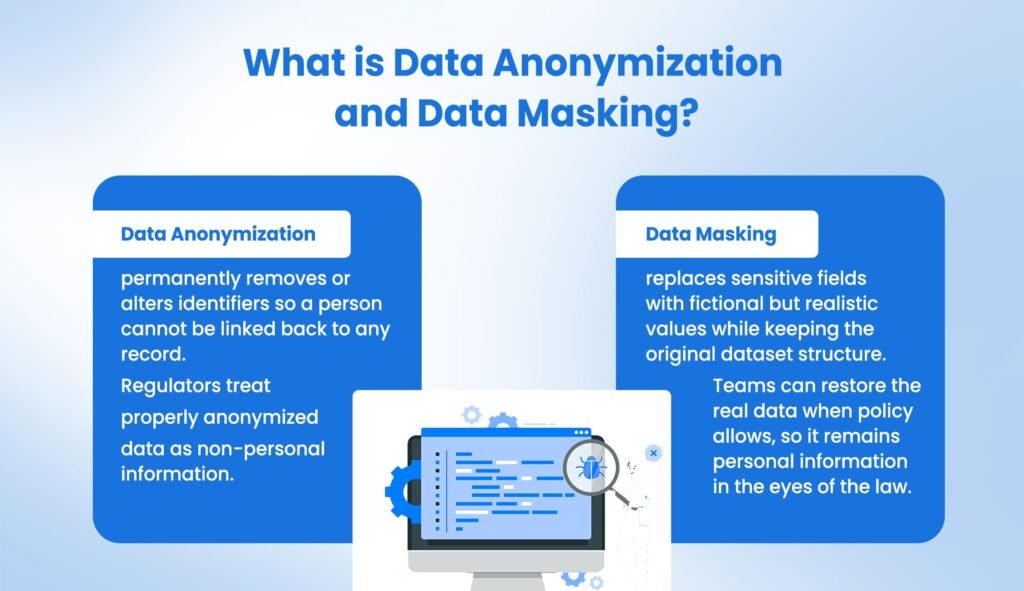
Data Anonymization permanently removes or alters identifiers so a person cannot be linked back to any record. Regulators treat properly anonymized data as non-personal information.
Data Masking replaces sensitive fields with fictional but realistic values while keeping the original dataset structure. Teams can restore the real data when policy allows, so it remains personal information in the eyes of the law.
These short definitions anchor the rest of the discussion on cost, risk, and compliance.
How Data Anonymization Works?
Anonymization starts with one goal: stop anyone from linking data to an individual ever again. Before any scrubbing begins, engineers often kick off a data capture scan to map every direct and indirect identifier inside the repository.
Core Process
First, privacy teams strip direct identifiers such as names and phone numbers, then destroy the keys that could unlock them. Next, they blur indirect identifiers—postcode, birth date, or job title—through grouping, perturbation, or aggregation so no combination traces back to one person. A quick parallel document digitization pass ensures paper records follow the same rules.
Common Techniques
Short opening sentence here.
- Hashing with salt, then deleting the salt
- k-anonymity or l-diversity grouping (age ranges, broader regions)
- Differential privacy noise that preserves trends but hides single rows
Compliance Fit
GDPR Recital 26 demands “reasonable” impossibility of re-identification. Firms prove compliance with risk scores that test whether attackers can break k-anonymity thresholds. Similar language appears in India’s DPDP Act and California’s CPRA.
Performance and Data Quality
Anonymization need not ruin analytics. Grouped ages or noise injection still power demand-forecast models. The trade-off is granularity, not usefulness.
Real-World Example
A health-tech start-up shares coronary data with a university. Names vanish, rare diagnoses merge into broader codes, and admission dates shift by a few days. Researchers keep statistical strength, yet nobody can trace a single patient.
Closing this section, anonymization frees data for collaboration while removing regulatory drag. Next, see where masking wins instead.

Cost, ROI, and Risk Considerations of Data Anonymization vs Data Masking?
Compliance is not free, but breaches cost more.
Direct Costs
IBM reports finance breaches average USD 6.08 million. GDPR fines can reach four percent of global revenue, and DPDP sets penalties up to INR 250 crore. Add legal fees, forensics, and churn to grasp full exposure.
ROI from the Right Choice
Anonymization eliminates repeated consent cycles for secondary studies, saving months of legal review. Time-to-insight drops, and product teams launch faster. A data automation layer often handles the heavy lifting.
Masking delivers realistic test data quickly. DevOps avoids manual scrubbing delays, so each sprint finishes sooner. Projects that rely on extracting data from pdf feed masked files straight into pipelines without extra prep.
| Scenario | Wrong pick | Correct pick | Financial impact (directional) |
| Share data with external researchers | Masking still counts as PII | Anonymization removes PII | Save legal fees and months |
| Continuous testing | Anonymization lacks realism | Dynamic masking | Faster release, lower bug cost |
| Anti-fraud model training | Masking only | Hybrid: mask then add noise | Cut bias, keep privacy |
Risk Beyond Money
Re-identification headlines damage trust and spark board scrutiny. A single misstep can trigger remediation work that dwarfs any preventive spend. Tools such as document classification spot sensitive fields in advance, slashing this hidden risk.
Final point: Look at privacy spending as avoided loss plus productivity gain. When the right layer is automated, firms usually see payback inside a year.
Emerging Privacy-Enhancing Technologies
AI-Generated Synthetic Data
Models learn dataset patterns then create new, fake records with zero real PII.
Homomorphic Encryption
Compute on encrypted data without decrypting it. Speeds keep improving.
Federated Learning
Algorithms travel to devices, train locally, and return only model weights. Personal rows never leave the source.
These options complement, not replace, anonymization and masking. KlearStack integrates them when policy demands even tighter control.
Why Should You Choose KlearStack?
Your privacy strategy should boost speed, not slow it. KlearStack combines template-free extraction with smart privacy rules in one platform.
What you get
- One engine applies anonymization or masking automatically.
- Self-learning AI reads invoices, policies, or medical forms with 99 percent field accuracy.
- APIs connect to Snowflake, SAP, and modern lakehouses in minutes.
Documented wins
- Up to 500 percent faster processing.
- 85 percent cost reduction in manual review.
- Audit logs for every data touch.

Conclusion
Permanent anonymization and reversible masking solve very different problems. Pick anonymization when data must travel outside your walls or when consent hurdles stall research.
Choose masking for internal testing and role-based views that need real-looking data without real risk. Mix both when anti-fraud models demand rich context but regulators demand low exposure.
Layer in invoice automation software to cut cycle times, and monitor ocr accuracy to keep each extraction precise. Finally, evaluate idp software options that apply policies automatically.
When combined with new privacy-enhancing technologies and guided by a clear five-question checklist, these steps will cut breach exposure, speed analytics, and satisfy regulators across three continents.
KlearStack’s template-free AI streamlines that blend, keeping privacy, speed, and savings in the same workflow for 2025 and beyond.
FAQ
Anonymization deletes identifiers forever, making datasets non-personal under GDPR and DPDP.
Masking swaps sensitive values with fakes that can be restored, so data stays personal.
Select masking for QA or support where structure must stay intact but secrets remain safe.
Yes. Our AI applies policy-driven anonymization or masking without templates or scripts.


