Document Fraud Detection AI: How Machine Learning Detects Forged Documents

Nasdaq’s 2024 Global Financial Crime report revealed that fraud losses reached $485.6 billion worldwide in 2023, with document fraud contributing significantly to these staggering numbers. As digitization accelerates across industries, fraudsters have evolved their tactics using AI-generated documents and advanced editing tools to bypass traditional verification systems.
- Are your verification processes equipped to catch fraudsters who forge bank statements in minutes using Photoshop?
- Can your team detect synthetic identities that combine real Social Security numbers with fabricated documents?
- How many forged paystubs slip through your manual reviews each month, costing your organization thousands in fraudulent loans or unauthorized access?
Traditional manual document checks cannot keep pace with the sophistication of modern fraud schemes. Organizations now face altered IDs, tampered metadata, and AI-generated documents that look virtually identical to authentic files.
The financial consequences extend beyond direct losses to include regulatory penalties, reputational damage, and erosion of customer trust. Modern intelligent document processing platforms integrate fraud detection capabilities to address these evolving threats.
Key Takeaways
- Document fraud detection AI analyzes pixel-level details, metadata, and structural patterns that manual reviews miss,
- identifying forgeries through machine learning algorithms trained on millions of documents
- AI systems detect multiple fraud types simultaneously, including photoshopped images, duplicate submissions, synthetic identities, and template-based forgeries across various document formats
- Automated verification reduces document review time while improving accuracy, enabling organizations to process high volumes without sacrificing security or compliance
- Advanced techniques like MRZ verification, EXIF analysis, and copy-move detection uncover subtle manipulation attempts that evade traditional inspection methods
- Real-time risk scoring prioritizes suspicious documents for human review, balancing automation speed with expert judgment for complex cases
- Integration with existing workflows through APIs allows seamless deployment without disrupting current operations or requiring system overhauls
What is Document Fraud Detection AI?

Document fraud detection AI refers to machine learning systems that analyze documents for signs of forgery, alteration, or fabrication. These systems perform multi-step processes including data extraction, anomaly detection, and verification to identify fraudulent documents before they enter organizational workflows.
AI-powered detection moves beyond simple visual inspection. The technology examines documents at multiple levels: comparing extracted text against established patterns, analyzing digital fingerprints for signs of tampering, and cross-referencing information against verified databases.
These systems leverage advanced data extraction techniques to convert unstructured document content into analyzable data points. Machine learning models continuously improve their detection capabilities by learning from new fraud patterns as they emerge.
Unlike rule-based systems that flag only known fraud types, AI adapts to evolving tactics. When fraudsters introduce new template designs or manipulation techniques, machine learning algorithms identify deviations from normal patterns without requiring manual rule updates. This adaptive approach addresses the fundamental limitation of static verification systems.
The technology processes various document types across industries. Financial institutions scan bank statements and tax forms, lenders verify income documentation and employment records, while government agencies authenticate identity documents and residency proofs. Each application requires different detection parameters, which AI systems handle through customizable verification workflows.
Organizations implement document fraud detection AI to address three core challenges: the volume of documents requiring verification, the sophistication of modern forgery techniques, and the need for real-time decisions during customer onboarding or transaction approval processes.
How Document Fraud Detection AI Works
The underlying mechanics of AI-powered fraud detection combine multiple technologies into a cohesive verification system. Understanding this workflow helps organizations appreciate both the capabilities and limitations of automated detection.
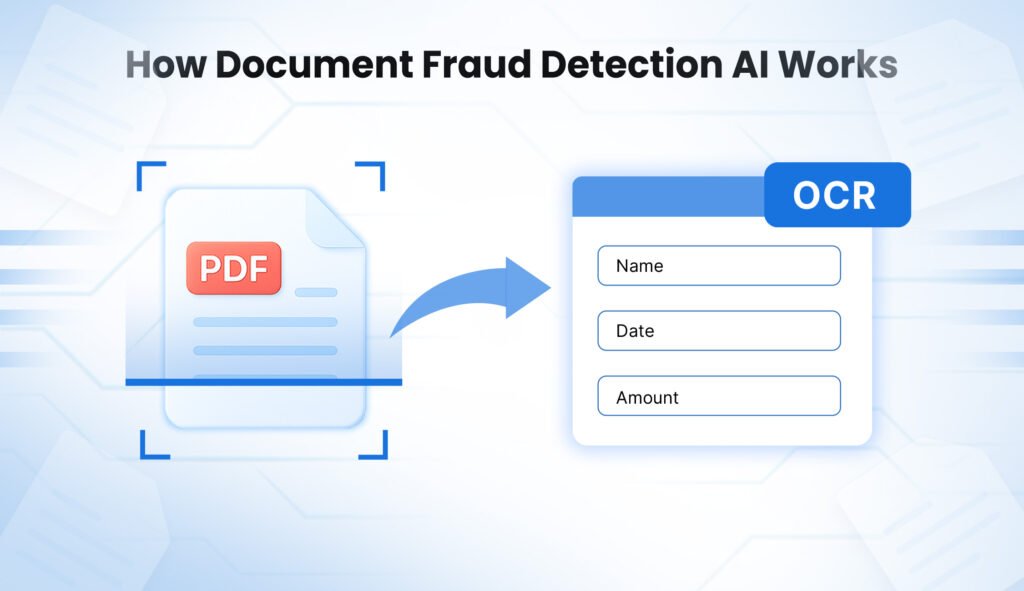
1. Data Extraction and Pre-processing
The process begins with Optical Character Recognition (OCR) converting scanned documents or uploaded images into machine-readable text. OCR technology identifies characters, numbers, and symbols regardless of document quality, font type, or scanning resolution. Organizations frequently need capabilities for extracting data from PDF files during the verification process to enable automated analysis.
AI enhances low-quality images before extraction. Algorithms sharpen blurry text, correct skewed angles, and remove background noise that interferes with accurate character recognition. This preprocessing step addresses a common fraud tactic where perpetrators deliberately submit poor-quality scans to obscure tampering evidence.
Once text extraction completes, the system structures the data into analyzable fields. Names, dates, amounts, and addresses become discrete data points rather than visual elements.
Understanding how to extract text from image files accurately forms the foundation of effective fraud detection. This transformation enables comparison across documents and validation against external databases.
2. Anomaly Detection Through Machine Learning
Machine learning algorithms establish baseline patterns by analyzing legitimate documents. The system learns what normal bank statements look like from a specific institution, including font choices, layout structures, and data formatting conventions.
When reviewing new submissions, algorithms compare document details against these baselines to spot inconsistencies. Mismatched fonts within a single document, unusual spacing between lines, or logos with incorrect proportions trigger anomaly flags. The system examines hundreds of visual and structural characteristics simultaneously.
Detection extends beyond visible elements. Algorithms analyze the relationships between data fields, checking whether stated income aligns with employment duration, or whether transaction histories match claimed account balances. Logical inconsistencies often reveal more about document authenticity than visual inspection alone.
3. Verification and Cross-Validation
Advanced systems verify person identity through biometric integration. Facial recognition compares photos on identity documents against live selfies, while liveness detection confirms the selfie subject is physically present rather than a photograph or video. Fingerprint matching adds another authentication layer for high-security applications.
Cross-validation techniques compare information across multiple documents submitted by the same individual.
Discrepancies between the address on a utility bill and the address on a driver’s license warrant investigation. Similarly, employment dates on a resume should align with tax return periods.
4. Risk Scoring and Prioritization
Documents flagged as suspicious receive risk scores based on the number and severity of anomalies detected. A single minor formatting inconsistency might generate a low score, while multiple red flags like altered metadata, mismatched fonts, and impossible dates produce high scores demanding immediate attention.
Risk scoring enables human reviewers to prioritize their efforts. Instead of manually examining every document, teams focus on high-risk submissions while automatically approving documents with clean verification results. This hybrid approach balances automation speed with human judgment for edge cases.
Types of Document Fraud AI Can Detect

Understanding the fraud types AI systems catch helps organizations configure detection parameters appropriate for their risk profiles. Different industries face different fraud vectors, requiring tailored approaches.
1. Document Forgery
Complete fabrication of documents represents one of the most brazen fraud attempts. Criminals create fake IDs, bank statements, or employment letters using template generators available online. These documents often appear legitimate at first glance but contain subtle flaws.
AI detects forgeries by comparing submitted documents against authentic examples. Machine learning models recognize institution-specific watermarks, security features, and layout patterns that forgers typically miss or replicate incorrectly.
Advanced document classification systems categorize documents by type and origin before applying appropriate verification protocols. Document structure analysis reveals when templates deviate from genuine formats.
2. Document Alteration
Rather than creating new documents, fraudsters modify legitimate ones by changing specific details. Photoshop and other editing tools enable alterations to names, dates, balances, or transaction histories. These modifications often occur on otherwise authentic documents, making detection more challenging.
Copy-move detection algorithms identify duplicated sections within documents, catching instances where signatures or stamps were copied from one area to another.
EXIF metadata analysis reveals when editing software opened and modified files, providing evidence of tampering even when visual changes appear seamless.
3. Synthetic Identity Fraud
This sophisticated approach combines real and fabricated information to create new identities. Criminals use legitimate Social Security numbers paired with fake names and addresses, submitting a mix of authentic and forged documents to pass verification systems.
AI addresses synthetic fraud through pattern recognition across document sets. Algorithms flag unusual combinations like newly issued identification documents paired with decade-old credit histories, or multiple applications using similar document templates with minor detail variations. Behavioral analysis supplements document verification by identifying suspicious submission patterns.
4. Template-Based Mass Fraud
Fraud rings exploit template generators to produce hundreds of fake documents with standardized formats. They submit bulk applications hoping volume overwhelms manual review capacity, knowing some percentage will slip through despite obvious similarities.
Duplicate detection assigns unique digital fingerprints to each processed document. When subsequent submissions share identical structures or formatting characteristics, the system flags them as potential template fraud.
Clustering algorithms group similar documents for investigation, revealing organized fraud schemes that individual document reviews might miss.
5. Pre-Digital Manipulation
Some criminals edit physical documents by hand, then scan or photograph them to create digital files that appear legitimate. Handwritten changes to printed documents evade simple software detection since the tampering occurred offline.
Grayscale analysis examines pixel intensity variations across document images. Handwritten alterations often show different ink densities, paper textures, or scanning artifacts compared to original printed text. Advanced image forensics detect these microscopic differences that human reviewers typically overlook.
What Documents Can AI Detect Fraud In?
Financial and identity documents represent the primary targets for fraud across industries, though virtually any document type can be verified using AI-powered systems.
Government-Issued Identity Documents
Passports, driver’s licenses, and national ID cards serve as primary identity proofs. Fraudsters forge these documents for identity theft, age verification bypass, or illegal immigration purposes.
MRZ verification checks the machine-readable zones on passports and IDs, validating checksums embedded in these coded sections.
Discrepancies between visual information and MRZ data indicate tampering. Biometric verification adds another layer by comparing document photos against live captures.
Financial Statements and Banking Documents
Bank statements prove account ownership and financial capacity for loan applications, rental agreements, and business partnerships. Altered balances, fake transactions, or fabricated statements from non-existent institutions appear regularly in fraud attempts.
AI compares submitted statements against known formats from legitimate financial institutions. Layout deviations, incorrect bank logos, or impossible transaction sequences trigger red flags. Cross-validation with actual bank records through secure data-sharing agreements provides definitive verification when available.
Employment and Income Verification
Paystubs and employment letters verify income claims for lending decisions and rental applications. Fraudsters inflate salaries, fabricate employers, or alter employment dates to qualify for services beyond their means.
Document structure analysis identifies fake paystubs generated from online templates. Algorithms verify employer information against business registries and tax databases. Logical consistency checks ensure reported income aligns with stated employment duration and position.
Legal and Contractual Documents
Contracts, property deeds, and legal agreements face manipulation risks in real estate transactions and business dealings. Altered signatures, changed terms, or backdated agreements create legal liabilities for organizations accepting fraudulent documents.
Signature verification algorithms analyze writing patterns, stroke pressure, and signature consistency across documents. Date analysis checks document creation timestamps against claimed execution dates. Metadata forensics reveal modification histories that contradict stated document origins.
Educational Credentials
Fake diplomas, transcripts, and professional certifications allow unqualified individuals to obtain positions requiring specific credentials. This fraud type threatens workplace safety and organizational competence.
AI verifies credentials by comparing document formats against verified examples from legitimate institutions.
Integration with educational databases enables direct confirmation of degree completion. Layout analysis catches common template-based degree mills that produce standardized fake certificates.
Benefits of Using AI for Document Fraud Detection

Organizations implementing AI-powered verification systems experience measurable improvements across operational, financial, and security dimensions. These advantages compound over time as systems learn and adapt.
- Real-time Processing Capacity AI automates document review processes that previously required hours of manual inspection. Systems verify documents within seconds during customer onboarding or transaction approval workflows. This speed enables organizations to maintain security standards without creating friction in user experiences.
Near-instantaneous verification allows real-time decision-making during high-stakes processes. Loan applications receive immediate preliminary approvals or rejections based on document authenticity.
Identity verification during account creation prevents fraudulent accounts from entering systems rather than discovering them after damage occurs.
- Superior Detection Accuracy Machine learning models identify subtle manipulations that evade human detection. Algorithms examine pixel-level details, metadata structures, and pattern consistencies simultaneously, catching forgeries that manual reviewers miss during visual inspection. Sophisticated AI document analysis capabilities process multiple verification layers concurrently for comprehensive fraud detection.
The technology detects fraud types beyond human capability. EXIF analysis reveals document editing histories invisible to the naked eye.
Copy-move detection identifies duplicated image sections across documents even when fraudsters resize or recolor copied elements. Metadata forensics uncover tampering evidence regardless of visual quality.
- Scalability Without Proportional Cost Increases Organizations processing thousands of documents daily cannot scale manual review teams proportionally. AI systems handle volume increases without corresponding staff expansions. A verification platform processing 100 documents daily can process 10,000 daily with minimal additional infrastructure costs.
This scalability proves critical during growth phases or seasonal volume spikes. Financial institutions onboard thousands of customers during promotional periods without compromising verification quality.
Insurance companies process claim surges after natural disasters while maintaining fraud detection standards.
- Consistent Application of Verification Standards Human reviewers experience fatigue, distraction, and subjective judgment variations. The same reviewer might flag a document as suspicious in the morning but approve an identical document in the afternoon after hours of repetitive review work.
AI applies identical verification criteria to every document regardless of processing time, reviewer workload, or document sequence. This consistency reduces false positives and false negatives caused by human factors.
Compliance teams demonstrate regulatory due diligence through documented, standardized verification processes.
- Adaptive Learning from Emerging Threats Fraudsters continuously develop new techniques to bypass detection systems. Rule-based verification systems require manual updates to address new fraud patterns, creating windows of vulnerability between technique emergence and system updates.
Machine learning systems adapt automatically as they process more documents and encounter new fraud attempts. Algorithms adjust detection parameters based on emerging patterns without requiring manual rule programming.
This adaptive capability maintains protection against evolving threats that static systems miss.
- Reduced Operational Costs Manual document verification requires significant staffing investments. Organizations employ teams of specialists to review submissions, investigate anomalies, and maintain verification quality. These teams represent ongoing operational expenses that scale with document volume.
Automation redirects human resources toward high-value activities requiring judgment and expertise. Instead of spending hours on routine verification, staff focus on investigating flagged documents, refining verification workflows, and addressing complex fraud schemes. Labor cost reductions often fund AI implementation investments within months.
Document Fraud Detection Techniques Used by AI
Modern AI systems employ multiple detection methods simultaneously, creating layered defenses that catch fraud attempts missed by individual techniques.
Duplicate Detection
Each processed document receives a unique digital fingerprint called a hash, calculated from document structure, content, and metadata. When identical or near-identical documents appear in subsequent submissions, the system flags them as duplicates. Automated data extraction workflows generate these fingerprints while extracting document content for analysis.
This technique prevents double payment frauds where criminals submit the same invoice or receipt multiple times with minor variations. In loyalty programs, duplicate detection stops users from claiming rewards repeatedly using slightly modified receipts.
The approach extends beyond exact matches. Fuzzy hashing identifies substantially similar documents even when fraudsters change formatting, resize images, or modify non-critical fields. This catches template-based frauds where perpetrators reuse document structures across multiple submissions.
1. Photoshop and Image Manipulation Detection
Copy-Move Detection Algorithms analyze image patterns to identify copied and pasted sections within documents. When fraudsters duplicate signatures, stamps, or logos from one document area to another, copy-move detection reveals these manipulations through pattern matching.
The technology works by breaking images into overlapping blocks and comparing each block against all others in the document. Identical or similar blocks in different locations indicate copying, even when fraudsters rotate, scale, or slightly modify duplicated elements.
EXIF Metadata Analysis Digital images and PDFs contain metadata recording creation dates, editing software, camera models, and modification histories. EXIF analysis examines this hidden information to detect tampering evidence invisible in document content.
When metadata reveals a document was created in Photoshop despite being presented as a scanned original, suspicion is warranted. Discrepancies between claimed document dates and actual file creation timestamps indicate backdating or fabrication.
Grayscale and Color Consistency Analysis Edited portions of documents often show subtle variations in pixel intensity, color saturation, or compression artifacts compared to unmodified areas. Grayscale analysis examines these microscopic differences across document regions.
Areas where text was digitally overlaid on backgrounds typically display different compression patterns than original text. Color consistency algorithms detect when fraudsters paste elements from multiple source documents, each carrying unique color profiles or lighting characteristics.
2. Cross-Validation and Data Matching
MRZ Verification for Identity Documents Machine Readable Zones on passports and IDs contain encoded data with built-in checksums for error detection. MRZ verification recalculates these checksums and compares them against encoded values, immediately identifying altered fields.
Fraudsters often change visible information on identity documents without updating corresponding MRZ data. This creates mismatches between what humans read and what machines decode, serving as definitive tampering evidence.
Multi-Document Data Consistency Checks Verification extends beyond individual documents to relationships between multiple submissions from the same applicant. Names, addresses, dates of birth, and employment details should align across different document types.
When a bank statement shows a different address than a utility bill supposedly from the same person, investigation is warranted. Similarly, employment start dates on resumes should match tax document periods and income statement timelines.
External Database Cross-Referencing Advanced systems query external databases to validate document claims against authoritative sources. Employer names can be verified against business registries, educational credentials against school databases, and addresses against postal records.
This real-time validation catches fabricated information regardless of document visual quality. Even perfect forgeries fail when claimed employers don’t exist or stated educational institutions have no record of degree conferral.
3. Template and Format Matching
AI systems maintain libraries of authentic document formats from various issuers. Submitted documents are compared against these verified templates to identify layout deviations, missing security features, or incorrect formatting.
Banks, government agencies, and other institutions follow standardized formats for official documents. Departures from these standards indicate forgery attempts, especially when combined with other red flags like metadata anomalies or data inconsistencies.
Format matching proves particularly effective against mass fraud schemes using template generators. Once the system identifies a fraudulent template pattern, it can flag all documents sharing that structure, potentially uncovering organized fraud rings.
Industries Most Affected by Document Fraud
Certain sectors face disproportionate document fraud exposure due to their reliance on paper-based verification, high-value transactions, or regulatory compliance requirements.
Banking and Financial Services Face Identity and Loan Fraud
Financial institutions process millions of documents annually for account opening, loan applications, and transaction verifications. Fraudsters target these organizations with forged identity documents, altered income statements, and fabricated bank statements to obtain credit or access accounts illegally. Modern OCR in banking applications incorporate fraud detection to verify documents during customer onboarding and loan processing.
Consequences extend beyond direct financial losses. Regulatory penalties for insufficient KYC procedures can reach millions when institutions approve fraudulent applications. Reputational damage from publicized fraud incidents erodes customer trust and impacts market valuation.
Lending and Mortgage Companies Combat Application Fraud
Mortgage fraud involving falsified income documentation, altered property appraisals, and fabricated employment histories costs lenders substantially. Fraudulent loans often default quickly, creating immediate losses compounded by foreclosure expenses and property value declines.
The sophistication of mortgage fraud schemes continues growing. Organized fraud rings submit bulk applications using synthetic identities and template-based documentation. Individual fraudsters use editing software to inflate income and assets, qualifying for mortgages beyond repayment capabilities.
Insurance Providers Battle Claims Fraud
False insurance claims involving doctored medical reports, fabricated damage assessments, and altered receipts drain insurer resources. These schemes inflate premiums for legitimate policyholders and create compliance risks when fraudulent claim patterns emerge.
AI-powered verification helps insurers validate claim documentation before issuing payments. Automated systems flag suspicious submissions for investigator review, reducing the percentage of fraudulent claims that receive payouts while accelerating legitimate claim processing.
Real Estate and Property Management Address Tenant Fraud
Landlords and property managers verify tenant applications using employment documentation, income proofs, and rental histories. Fraudsters submit edited paystubs, fabricated employer letters, and forged rental references to secure properties they cannot afford.
Tenant fraud creates expensive consequences. Eviction processes consume time and legal expenses when fraudulent tenants default. Property damage and lost rent compound direct fraud costs. AI verification during application screening prevents problematic tenants from entering properties.
Human Resources Departments Combat Credential Fraud
Fake diplomas, altered transcripts, and fabricated references allow unqualified candidates to obtain positions requiring specific credentials. This fraud threatens workplace safety in regulated professions and creates liability risks when credential fraud is discovered post-hire.
Background verification services increasingly incorporate AI document analysis to catch credential fraud during hiring processes. Automated verification against educational databases confirms degree authenticity before employment offers extend, protecting organizations from negligent hiring liability.
Healthcare Organizations Fight Prescription and Insurance Fraud
Forged prescriptions enable illegal medication access, while fake insurance documents allow unauthorized treatment. These fraud types endanger patient safety and create compliance violations for healthcare providers processing fraudulent documentation.
Document verification integrated with prescription management systems prevents forged prescriptions from being filled. Insurance verification during patient intake flags fake coverage documentation before treatments commence, protecting providers from unreimbursed care costs.
Why Should You Choose KlearStack?
KlearStack delivers intelligent document processing with AI-powered fraud detection built specifically for organizations requiring both speed and security in document verification workflows.

Comprehensive Fraud Detection Across Multiple Vectors
The platform employs duplicate detection, photoshop analysis, MRZ verification, and metadata forensics simultaneously. This layered approach catches fraud attempts that single-technique systems miss. Whether facing template-based mass fraud or sophisticated individual forgeries, KlearStack’s algorithms identify anomalies at pixel, structure, and data levels.
Advanced image forensics detect copy-move manipulations, EXIF tampering, and grayscale inconsistencies invisible to manual reviewers. Cross-validation engines compare data across document sets, flagging synthetic identities and logical inconsistencies before fraudulent documents enter workflows.
Seamless Integration with Existing Workflows
Organizations implementing KlearStack maintain current systems while adding verification capabilities. API-driven architecture connects with document management platforms, CRM systems, and approval workflows without requiring infrastructure rebuilding.
The platform processes documents in real-time during customer interactions, providing immediate verification results that support instant decision-making. Integration flexibility allows gradual automation expansion, starting with high-risk document types and extending coverage as teams gain confidence.
Customizable Verification Rules for Industry-Specific Needs
Different industries face different fraud patterns requiring tailored detection approaches. KlearStack allows organizations to configure verification parameters matching their risk profiles and document types.
Financial institutions configure strict verification for loan documents while maintaining lighter checks for informational submissions. Healthcare providers prioritize prescription verification while property managers focus on income documentation. Custom rule engines adapt verification rigor to context without sacrificing underlying detection capabilities.
Multi-Language and Multi-Format Support
Global operations process documents in dozens of languages and formats. KlearStack’s OCR technology handles multilingual documents without requiring separate processing pipelines for each language.
The system processes PDFs, images, scanned documents, and digital files equivalently. Format variations don’t impact detection accuracy, enabling consistent verification regardless of how documents reach the organization.
Real-time Risk Scoring and Prioritization
Every processed document receives a risk score reflecting detected anomaly severity and quantity. High-risk documents automatically route to human reviewers while low-risk submissions receive immediate approval.
This prioritization balances automation efficiency with expert judgment for complex cases. Organizations reduce manual review workload by focusing human resources on genuinely suspicious submissions rather than examining every document indiscriminately.
Continuous Learning and Adaptive Detection
Machine learning models improve continuously as they process more documents. The system learns from flagged documents, confirmed frauds, and false positives, refining detection parameters automatically.
Organizations benefit from improving accuracy over time without manual model retraining. As fraud techniques evolve, KlearStack’s adaptive algorithms adjust detection approaches, maintaining protection against emerging threats.
Compliance-Ready Documentation and Audit Trails
Regulatory requirements demand documented verification processes and decision audit trails. KlearStack maintains complete processing records showing what checks were performed, which anomalies were detected, and what risk scores were assigned.
These audit trails support compliance demonstrations during regulatory examinations and provide defensible documentation when fraud incidents require investigation or litigation. Automated record-keeping reduces compliance burdens while ensuring thorough documentation.
Ready to protect your organization from document fraud? Schedule a demo to see how KlearStack’s AI-powered verification identifies forgeries, prevents synthetic identity fraud, and stops fraudulent documents before they create financial losses.
Conclusion
Document fraud detection AI represents a fundamental shift from reactive fraud discovery to proactive prevention. Organizations implementing machine learning verification systems catch forgeries during submission rather than discovering fraud after damages occur. The technology processes documents at scales and speeds impossible through manual review while detecting subtle manipulations that human inspectors miss.
Organizations delaying AI adoption face growing vulnerabilities as fraud techniques advance. Criminals use the same AI technologies to create more convincing forgeries, generate synthetic identities at scale, and automate fraud attempts.
Maintaining security requires matching fraudster sophistication with equally advanced detection capabilities. The question is not whether to implement AI-powered verification, but how quickly organizations can deploy these essential protections.
FAQs
Modern AI systems include image enhancement preprocessing that improves document quality before analysis. Algorithms sharpen blurred text, correct skewed angles, and remove background noise, enabling accurate character recognition even from low-resolution scans.
AI systems verify virtually any document type including identity documents, financial statements, employment records, contracts, receipts, invoices, educational credentials, and legal agreements. The technology adapts to different formats, languages, and structures through customizable verification workflows.
Processing times typically range from seconds to under a minute per document depending on complexity, image quality, and verification depth required. Real-time systems provide immediate preliminary results during customer interactions, with more thorough forensic analysis completing within minutes.


